blog
Greymatter and Cybersecurity Mesh Architecture: Support at the Operation Dashboard Layer
How Greymatter enables the Cybersecurity Mesh Architecture Operational Dashboard Layer.

August 16, 2023
By the Greymatter Technology, Innovation, and Outreach Team
Gartner predicts that by 2024, organizations adopting Cybersecurity Mesh Architecture (CSMA)1 will reduce the financial impact of individual security incidents by an average of 90%. Over the past several weeks we’ve described how the Greymatter Application Networking Platform helps customers capture these savings with support for CSMA’s security analytics and intelligence, identity fabric, and centralized policy, posture, and playbook management layers. In this blog, we explain how Greymatter supports the fourth and final layer: the operational dashboard.
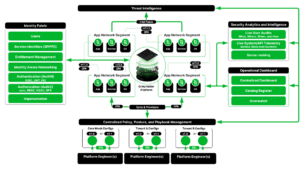
Figure 1: CSMA and Greymatter
Why now
In today’s multi-cloud and hybrid environments many organizations have different security teams responsible for network, cloud, and endpoint security. Each team tends to use its own set of tools which operate independently and do not communicate with each other. And each tool has its own visualization, alerting, and reporting capabilities.
A lack of holistic visibility into the overall security posture and health across the enterprise makes it difficult to detect inconsistent controls and policies, and misconfigurations that weaken security posture. Fragmentation also creates inefficiencies in incident detection, response, and mitigation, as security teams need to manually gather and analyze data from multiple sources to identify patterns, anomalies, and potential security threats.
Through integration and interoperability, the CSMA operational dashboard layer aims to facilitate the creation of comprehensive sets of views that break down silos and empower different security teams to proactively protect their environments and detect upcoming trends or threats before any damage occurs. Serving as a jump point into the security ecosystem, the dashboard layer enables swift and effective response to security events.
Why Greymatter
Greymatter’s unified and intuitive platform unlocks the full potential of the operational dashboard layer, delivering a single-pane-of-glass view and powerful audit capabilities for visibility and understanding across multi-cloud and hybrid environments. Teams can more easily collaborate, manage, and maintain a cohesive security posture and coordinate actions. Here are a few top use cases.
Fraud prevention
In 2022, 70% of financial institutions2 lost more than $500,000 to fraud, with 91% reporting a year-over-year increase since 2021. With costly losses at record highs, banks need to enhance their fraud prevention systems with additional insights into customer behavior patterns, login attempts, and user activity to detect any suspicious or fraudulent activities. Greymatter enables a proactive approach to fraud prevention, enhancing audits without the need for any code instrumentation. Real-time monitoring of user activities and interactions provides valuable data that can be fed into fraud prevention systems to identify and prevent unauthorized access attempts. Efficient collaboration and communication among different teams enables integration and coordination in fraud prevention efforts across the organization.
Threat monitoring and detection
The Executive Order3 addressing Zero Trust and compliance prioritizes the ability to monitor and detect cyber threats in real-time and is a best practice that should be heeded not only by federal government agencies, but by any enterprise engaged in mission critical activities, including banking, telecommunications, and supply chain. But in a world where deployments are multi-theater, threat intelligence monitoring, early detection of network intrusions, malware infections, and insider threats are incredibly difficult to address given limited insights into distributed applications, services, and APIs across many, different infrastructures. These challenges are just as valid for enterprise-scale, highly regulated private industries. Greymatter provides a comprehensive view of the application ecosystem and real-time intelligence into what’s happening to visualize access patterns and behaviors and identify anomalies.
Secure Day 2 operations
As software is deployed and enters operational use, the ability to monitor and manage security in production environments becomes more crucial but less visible and hard to track. Greymatter provides visible insights, including from the individual health of a service, down to its memory and CPU utilization, even the get/put methods being traversed through the network. This level of data enables real-time status of system logs, security events, and user activities, as well as ensures continuous threat detection and incident response during the DevSecOps lifecycle. Developers can proactively maintain compliance with security standards, regulations, and policies and mitigate risk by automating patch management frameworks in the CI and CD phases of deployment.
How Greymatter does it
Greymatter is the first application networking playbook with over 100 out-of-the-box automation defaults for security, application, and API insights. As an application networking platform, Greymatter provides robust support for the CSMA operational dashboard layer leveraging Catalog Register and Overwatch capabilities to offer data, insights, and audits of who is doing what, when, where, and how, all available through a Centralized Dashboard. Specifically:
- Greymatter enables consolidation of intricate policy files into a centralized hub and then, with under 10 lines of code, reference that policy for effortless fleet-wide updates across applications, APIs, and data services – regardless of cloud or hybrid infrastructure. Through a Centralized Dashboard, Greymatter provides a holistic view of the entire application networking infrastructure. This includes unparalleled visibility and control across multi-cloud and hybrid environments and is inclusive of applications, services, databases, data stream services, and more. The single-pane-of-glass view enables organizations to quickly assess the health, status, and performance of their network assets. Gaining valuable insights into their operational environment, organizations can make informed decisions, troubleshoot issues more efficiently, and optimize resource allocation for improved operational efficiency.
- Network or cloud environments can stay one step ahead with our unrivaled capability to effortlessly integrate immediate forensic user tracking audits with zero configurations needed, ultimately enhancing security and compliance across applications, APIs, and services with ease. We streamline API management with Catalog Register. This enables developers and administrators to easily discover, organize, and document their APIs and services and programmatically integrate with other systems and tools. The robust catalog encompasses all operationally running network assets for visualization in one dashboard, empowering teams to efficiently manage and leverage their resources.
- Our powerful Overwatch capability offers real-time insights into the activities taking place within the network, including within multi-tenant spaces for separation of concern. Integration with the centralized dashboard provides a unified view and comprehensive understanding of who is involved, what actions are being performed, where they are occurring, when they are happening, and how they are being executed. Customers gain the power to seamlessly view multiple application mesh networks in a unified interface, featuring health status, dependency lists, and comprehensive search capabilities across clouds. Insights include:
- Real-time health heuristics for proactive monitoring and detection of potential performance issues or anomalies to get ahead of potential service disruptions or degradation.
- Application insights, audits, and scorecards to assess the operational performance of applications or services by route or user. These assist in informed process optimization decision-making and help strengthen security within your network.
- Business intelligence and scoring for insights into the business implications of distributed services and data. These are crucial to evaluating cost increases versus reductions, optimize resource consumption, and even make informed decisions about allocating development and engineering time.
Additional capabilities include integration with the other layers of the CSMA framework to ensure smooth information flow and coordination between different security functions. This also includes integration with existing cybersecurity infrastructure, such as SIEMs and SOARs, feeding deep insights that can be leveraged to improve threat detection and response and increase ROI of complementary tool sets.
What’s in it for our clients
Our clients gain meaningful value from our early support for CSMA’s operational dashboard layer, including:
- Improved threat detection, response, and real-time analysis with data streams, audits, and insights that enable deeper understanding of the who, what, when, where, and how of activity within the application ecosystem across the entire environment, and fuel faster, comprehensive actions to improve security posture and risk mitigation.
- Centralized management enabled by unified views and powerful auditing capabilities of applications, services, and APIs, empower teams to conduct analysis from the tactical to the strategic level, make more informed decisions, and improve security and business operations.
- Increased collaboration by breaking down silos between teams and tools with access to shared data and visualizations that facilitate communication and coordinated response.
As we continue to address the challenge of team silos resulting from diverse infrastructures and disparate tools, we will further enhance interoperability and seamless communication with other security intelligence systems. Greymatter users can also expect continued cultivation of our intuitive user interface and additional capability to ingest and leverage feedback from various tools to develop proactive deployment strategies for incident response and compliance.
Contact us today to schedule your free consultation, determine your microservices maturity level, and build a reference implementation architecture to begin moving your organization up the microservices maturity model to accelerate software delivery and increase speed to market, while ensuring security.
Further reading:

